Every day we see more and more digital trends cropping up in every sector, showing that technology is here to stay. For the nonprofit sector and individual fundraisers, the expansion to the online space has helped fundraising grow to new heights that were once unfathomable.
Today, individuals and organizations can effortlessly expand and capitalize using their online networks, all thanks to
the growing digital fundraising sphere.
Fundraiser websites can be used for personal fundraising to cover medical expenses, tuition costs, or other worthy causes. Similarly, cause-based organizations employ these online solutions to fund their work and continue striving toward their missions.
But with so many options to choose from, it can be challenging to decide which fundraiser website to invest in. To give you a headstart, we've put together a list of the 14 best solutions, which we'll explore in-depth:
Donately | Best Online Fundraising WebsiteDouble the Donation | Top Fundraiser Website for Matching GiftsDonorSearch | Best Fundraiser Website for Prospect ResearchBonfire | Best T-Shirt Fundraiser SiteShopify | Best Fundraiser Website for eCommerceSendGrid | Top Fundraiser Website for Custom Follow-UpPatreon | Best Membership Fundraiser WebsiteWebflow | Best Fundraiser Website for Web DevelopmentInstapage | Top Fundraiser Website for Landing PagesSquarespace | Best Fundraiser Website for Content MarketingExperiment | Top Fundraiser Website for Scientific ResearchIndiegogo | Top Fundraiser Website for Creative ProjectsEdco | Best School and Team Fundraiser WebsiteKiva | Top Microlending Fundraiser WebsiteABC Fundraising | Best Product Fundraising WebsiteKeep in mind that some of the best fundraising websites are quite specific in terms of projects and causes, while others are much more open in format. When searching for the right solution, we recommend you take a platform-based approach and select the fundraiser websites that are most relevant to your needs.
Without further ado, let's kick things off with our top pick:
Donately!

1. Donately | Best Online Fundraising Website
The digital space opens the door to a world of possibilities for fundraisers as well as prospects who are looking to make a philanthropic impact.
Donately offers the online fundraising tools you need to maximize the online donor experience and boost revenue.
We recognize the potential that lies in the online space. Through our fundraising software, we provide easy-to-use tools to harness that power. Easily embed our donation forms into your existing website, set up your own peer-to-peer fundraising and crowdfunding campaigns, and much more. This way, you can focus on tweaking your messaging to boost awareness for your cause.
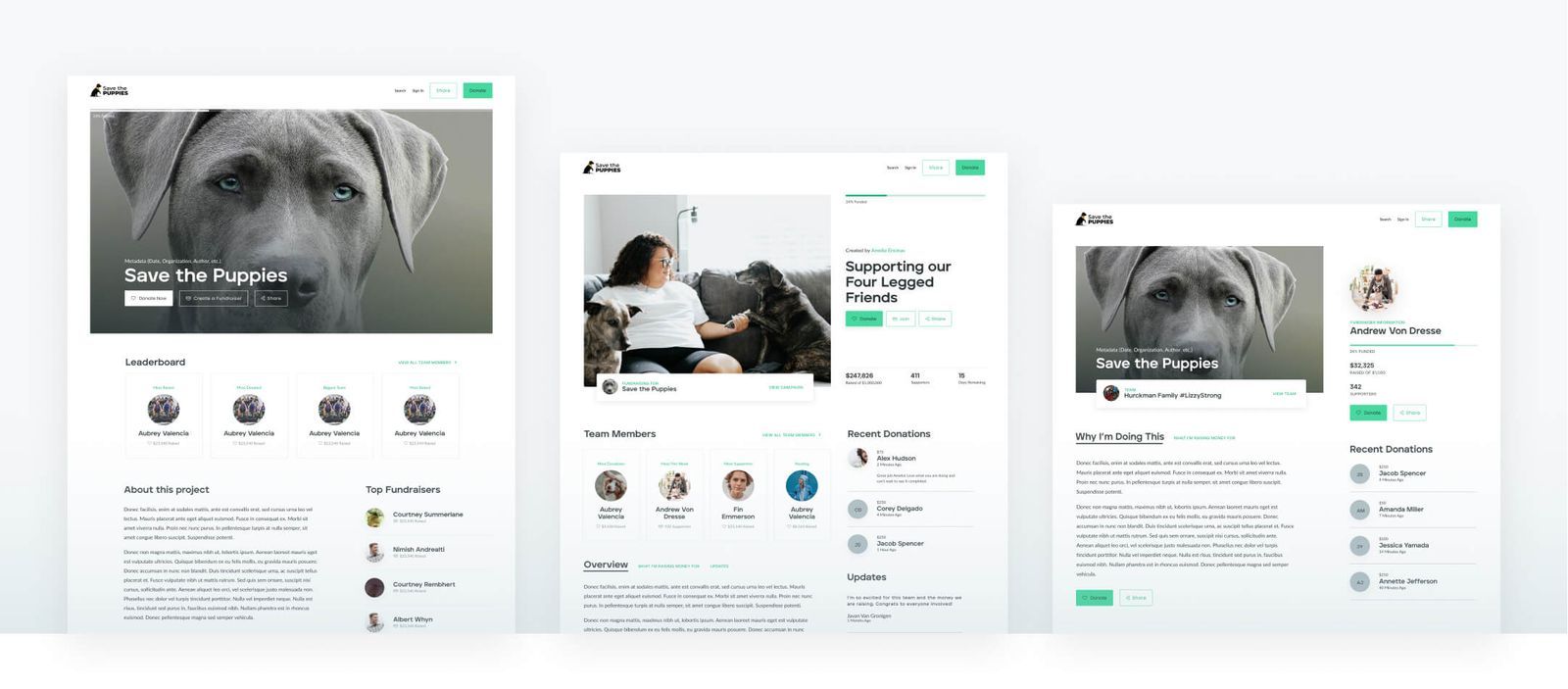
How This Fundraising Website Can Help
When you partner with Donately, you can rest assured that all your online fundraising tech needs will be covered. Let's briefly walk through
our core features that will enhance both your donors' experience and your teams' experience:
Mobile-Responsive Donation Forms: Configure your online donation forms to suit your exact needs. Our fundraising website allows you to collect donor information, set suggested donation amounts, promote recurring donations, pass processing fees to your donors, and more. Best of all, our donation forms and pages are mobile-responsive, meaning donors have the added convenience of donating from any device.
Peer-to-Peer Fundraising: Leverage your supporters' networks with peer-to-peer fundraising tools. We designed our fundraising page technology so that your organization can tell its story while your volunteer fundraisers also add their personal connections to further drive donations.
Donor Data: Gain valuable insights about your supporters and about the effectiveness of your online donation tactics to optimize your efforts. Instantly filter your data to view key metrics, such as your most active donors, popular donation amounts, and the effectiveness of your online campaigns—all on one convenient dashboard.
Text Messaging: With Text-to-Donate, supporters can skip numerous steps and donate just by texting. Set up a phone number and designated keyword, and donors will recieve a link to your donation page immediately after texting the keyword. Along with enabling Text-to-Donate, our text messaging features allow you to communicate key updates to your donors, send sign-up pages, and more.
Best of all, we offer
numerous integrations, several of which we'll cover throughout this article. This way, you can connect all of your software and fundraising websites for a more harmonious experience.
2. Double the Donation | Top Fundraiser Website for Matching Gifts
Corporate giving programs—
matching gift programs in particular—represent a major fundraising opportunity for the nonprofit sector. Through these programs, companies offer to match their employees’ philanthropic donations to eligible nonprofits, typically at a dollar-for-dollar ratio. This means you can potentially double the contributions you're already receiving.
Make sure you don’t miss a single dollar in available matching gift revenue by using a fundraiser website tool like
Double the Donation, which helps you locate these existing opportunities. Easily embed the tool on your fundraising website to maximize your incoming donations. Plus, its autosubmission functionality simplifies the process of submitting a request for your donors.
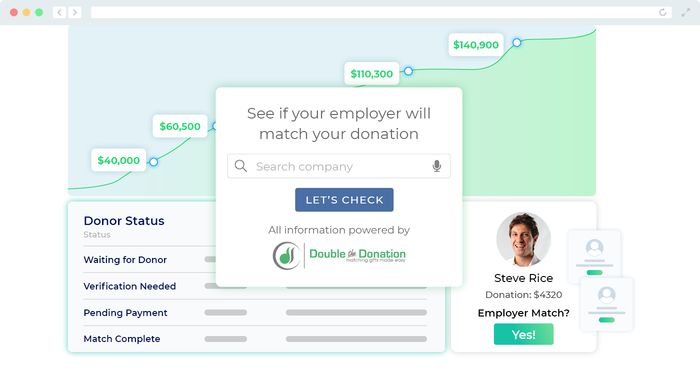
How This Fundraising Website Can Help
With a database that compiles information on 24,000+ companies and subsidiaries, Double the Donation offers the industry’s leading matching gift search tool. Here’s how the matching gift process works with this nonprofit fundraising website tool by your side:Your nonprofit embeds the search tool into your fundraising website's donation page or confirmation page.
A donor types the name of their employer and hits “submit.”
The fundraising tool provides all available information regarding the employer’s program.
If eligible, the donor clicks through to the form and submits the match request to their employer.
With
Double the Donation’s integration with Donately, locating these opportunities is easier than ever before. You can identify eligible donors directly from the donation process and use automated, customizable outreach strategies to follow up with them post-donation.
For those with a substantial donor base (and therefore more data), Double the Donation offers a more robust system:
360MatchPro. This fundraising website tool fully automates the match-finding process for organizations that already raise more than $25,000 in matching gift funds each year, reducing the amount of manual labor needed to secure these contributions.
When you
enable the autosubmission functionality, donors can automatically submit their corporate match request to their employers from your confirmation page. After the donor checks a box, the tool will check their donation’s eligibility for autosubmission and submit a request to their employer on their behalf. No more forms to fill out. A simpler process for donors means more people will follow through!

3. DonorSearch | Best Fundraiser Website for Prospect Research
Prospect research is a vital component of any effective fundraising strategy. It provides insight into who your donors (and potential donors) are and what drives them to give. However, conducting this research manually is possible but not at all an efficient use of time, especially for larger organizations with numerous supporters. Because of this, you'll need the right tools to streamline the process.
DonorSearch's dedicated fundraising website tools help to accomplish exactly that, so organizations can focus on leveraging data in smarter ways. This way, you'll invest your efforts into creating hyper-personalized outreach, rather than spending all your time collecting metrics.
How This Fundraising Website Can Help
With DonorSearch, your team will have access to the nation's largest philanthropic database of 150+ million records (with 500,000 new records added each week). Because of this, you'll gain insights you won't find anywhere else.
Let's explore how DonorSearch’s online prospect research platform plays into developing more tailored fundraising outreach:Wealth Screening: Discover details about your prospects, such as business and foundation affiliations, real estate, past giving history, and more.
Top Prospect Verification: DonorSearch is the only wealth screening company that will manually verify top prospects to maximize accuracy. Their prospect researchers will review any records you select.
Marketing Lists: Create targeted marketing lists based on more than 300 financial, demographic, and interest categories, so you can reach out confidently knowing you're contacting the best recipients.

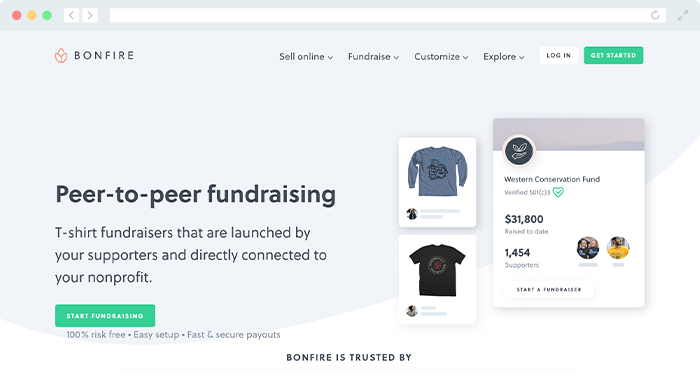
4. Bonfire | Best T-Shirt Fundraiser Site
Branded merchandise, like t-shirt fundraising, can help you connect with supporters, whether it’s coordinated with
an event or hosted as a standalone fundraiser. By creating products that appeal to their interests, supporters will be excited to donate to your worthy cause. Plus, those who feel particularly connected to your work will be proud to sport your brand, which is a conversation starter when they wear the merchandise in public.
Bonfire's fundraising website allows individuals and nonprofit organizations alike to sell custom t-shirts. Using their mobile-friendly, customizable campaign pages, you can reach supporters, share your story, and raise funds without a struggle. This fundraiser website enables you to create a dedicated online store where you can centralize all products, making it incredibly easy for your supporters to browse your custom apparel.
How This Fundraising Website Can Help
Whether you're
a nonprofit professional or
a personal fundraiser, Bonfire's fundraising website can help you reach supporters in a new, exciting way. All you need to do is design your product, set your prices, and launch your fundraiser.
Bonfire offers extensive custom apparel options that come in a variety of styles, fits, and colors for you to bring your vision to life. It's free to get started, although there are a few required costs, including:Donation Fee: If you enable the donation option to be displayed at checkout, Bonfire will deduct an 8% fee for transaction costs. The other 92% goes directly to you. For certified nonprofits, this fee decreases to only 3.5%.
Base cost: Each product's base cost is determined by its manufacturing, sourcing, and printing expenses. To decrease your based costs, simplify your t-shirt design.
Shipping: Domestic shipping starts at $3.99 for the first product, and each additional product within the same campaign is decreased to $2.50 each. For international orders, shipping is $9.99 for the first product, and each additional product from the same campaign is decreased to $4.00 each.

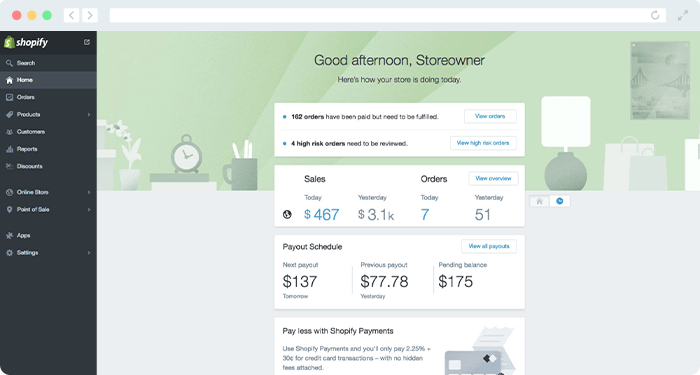
5. Shopify | Best Fundraiser Website for eCommerce
While nonprofit revenue traditionally comes from donations and sponsorships, a storefront can be incredibly appealing to donors. Online stores condense all your branded products into one convenient location, allowing you to simplify the process and reach more donors altogether.
Through
Shopify's online fundraising website, your team can select from a diverse range of products and compile them into an attractive online store. Their customizable themes make it easy to get up and running. Plus, Shopify offers affordable rates for nonprofit and exceptional customer service, so you can seamlessly reach supporters around the globe.
How This Fundraising Website Can Help
Shopify's eCommerce platform allows you to develop an attractive storefront so your cause is represented exactly how you envision it. Through this nonprofit fundraising website, you'll be able to accept donations, sell internationally, and analyze fundraising growth in real-time so you can refine your efforts as you go. With more than
4.4 million+ active users, you'll expand your audience in no time.
Available on all Team & Enterprise plans,
Shopify's integration with Donately takes this fundraising website's effectiveness one step further. You'll be able to embed
a donation form directly into your Shopify store, maximizing your online fundraising potential.

6. SendGrid | Top Fundraiser Website for Custom Follow-Up
Email messaging drove
28% of all online revenue in 2017, making it a crucial outlet when conducting online outreach. The timeliness of your follow-up post-donation goes a long way in making online donors feel valued and can mean the difference between securing that sought-after second donation or losing their support altogether.
With all that rides on your outreach, it's important to invest in an intuitive email system.
Sendgrid's fundraising website enables you to provide a best-in-class experience for your recipients. This robust system allows nonprofits to send customized transactional emails that provide value to your supporters and encourage them to keep returning.
How This Fundraising Website Can Help
With more than 60 billion emails sent every month through their services, Sendgrid is a trusted resource that has the expertise needed for optimized communications. Here are a handful of benefits this fundraiser website offers to
improve the emailing experience for all sorts of causes:Email Automation: Create personalized experiences that are scalable and relevant to each donor. Devise a warm welcome with an
automated onboarding series, nurture attendees prior to an event, and follow up with leads who interact with your content.
Responsive Templates: Save time customizing messages with responsive designs that are optimized to drive results on any device. Easily edit content and customize it with your logo and brand colors without breaking the design of the overall page.
A/B Testing: Determine what content is most effective with A/B testing tools. Compare various design elements and refine your emails to best suit your audience and drive results.
Through this fundraising website, you can
integrate with Donately to supercharge your donation receipts. Quickly customize your thank-you emails with custom HTML, which will pull in individuals’ details directly from your donations.

7. Patreon | Best Membership Fundraiser Website
With the constant obstacles thrown in the direction of the nonprofit sector, it's important to develop a consistent revenue stream. Memberships are an effective way to accomplish this as they allow you to create a sustainable base of support and cultivate lasting relationships. Because
membership programs pose major benefits, you'll need an intuitive membership-based fundraising website, like Patreon.
Patreon is a fundraising website that lets your passionate advocates support your work. Whether an individual creator or a nonprofit organization, this fundraiser website offers member-based tools that allow you to connect with your most valuable supporters and grow your community.
How This Fundraising Website Can Help
With 150,000+ creators on this fundraising website, creating (or revamping)
an engaging membership program will be a breeze. This platform is ideally suited for content creators like podcasters, video developers, and writers. Patreon has also tailored its membership services to the nonprofit sector using these core features:Exclusive forums. Gauge your members' experiences by giving them the opportunity to collaborate and provide feedback for strategic improvement.
Messaging tools. Engage with your members and build a sustainable community by chatting directly with members.
Create exclusive opportunities. Offer valuable content by
live streaming exclusively to your members to convey gratitude for their ongoing support.

8. Webflow | Best Fundraiser Website for Web Development
A nonprofit's website is its
digital marketing strategy's biggest asset. It houses all details about your cause, including key initiatives and how visitors can get involved. A well-designed nonprofit website will help you connect with the right prospects, build brand awareness, and drive conversions. Before you can do this, you'll need to invest in an effective website builder, like
Webflow.
Webflow's website builder empowers nonprofits to design and build professional websites without help from a professional developer. It's free to get started and allows you to fully control design elements without paying a dime. Although, upgrading to a paid plan gives you access to additional features that can supercharge your online fundraising efforts.
How This Fundraising Website Can Help
Using Webflow, you'll be able to launch an immersive website for your cause, whether for a nonprofit or a personal fundraiser, that garners attention and resonates with visitors. With Webflow's development tools, your team will be able to:Edit content from the front end and build production-ready websites without extensive coding.
Customize your design from end-to-end with custom fonts, color swatches, and more.
Improve your SEO by editing meta titles and descriptions to signal to search engines the topic of site pages without needing to install additional plugins.
With 100+ hours of tutorials, Webflow ensures you have all the educational resources you need to become an expert and get up and running with your nonprofit's fundraising website. Best of all, you can
integrate with Donately to embed
a donation form directly onto any Webflow website and page.

9. Instapage | Top Fundraiser Website for Landing Pages
According to
Nonprofit Tech for Good, around 34% of nonprofit organizations have paid for social advertising. When clicked on, these promotional materials drive traffic to post-click landing pages. To ensure your paid advertising doesn't go to waste,
strong landing pages are vital for success.
Because of this, you'll want to employ the help of a fundraiser website dedicated to creating engaging campaign landing pages, like
Instapage. Instapage offers best-in-class tools that empower nonprofits to develop beautiful landing pages for their campaigns. Whether you're creating a
peer-to-peer campaign signup page or a volunteer form, this fundraiser website will help you create conversion-optimized landing pages.
How This Fundraising Website Can Help
When promoting your cause via social media, email, or your website, Instapage drastically simplifies the development process. Let's explore how
this fundraiser website's features can help you optimize your fundraising strategies:Customize responsive pages and forms that match your brand within minutes.
Collaborate in real-time with your team to hasten the review process and push your landing pages live.
Pick from 500+ customizable layouts to quickly launch a professionally-designed landing page built specifically for the nonprofit industry.
Create beautiful, high-converting pages with the intuitive drag and drop builder.
When crafting your landing pages, you'll be able to embed a
Donately donation form onto all of your landing pages, thanks to
the intuitive integration. Then, use their A/B testing tools to measure efficiency and perfect your donation form.

10. Squarespace | Best Fundraiser Website for Content Marketing
Research from the Content Marketing Institute found that 92% of nonprofit professionals use content marketing and for good reason. Developing meaningful content helps readers connect with your cause, drives them toward your campaigns, and encourages them to contribute. However, studies have also found that
50% of nonprofits indicate that they lack the time to create content for their website.
Squarespace recognizes these challenges and in turn developed a nonprofit fundraising website that streamlines the content creation process altogether. Squarespace is a world-class fundraising website platform that's trusted by hundreds of nonprofits looking to spread their mission and collect donations. This way, you can turn your engaging ideas into a reality while also building your online presence.
How This Fundraising Website Can Help
While built for many sectors, Squarespace is a versatile website builder that enables you to share your valuable content with supporters. Let's dive into their core features that can improve the creation process and put you on the path to successful content marketing:Blogging. Share thought leadership, industry insights, and motivational stories about supporters, staff, beneficiaries, and anyone else who’s involved in your work. Categorize, share, and schedule your posts to make your content stand out to readers.
Built-In SEO Tools. Every Squarespace fundraising website comes with a suite of integrated features and useful guides for nailing down search engine optimization best practices.
Social Media Integrations. Leverage your supporters' networks with social media integrations. As you develop compelling content, you'll be able to disseminate it via social media with convenient share buttons.
In-Depth Analytics. Learn where your traffic is coming from, and determine which content attracts visitors and which isn't quite meeting expectations based on insightful engagement metrics.
Through
its integration with Donately, you'll be able to embed
a donation form directly into your site and enhance the style of your form to match your Squarespace site design to a tee.

11. Experiment | Top Fundraiser Website for Scientific Research
Just like any other nonprofit, research institutions must receive adequate funding in order to continue their work and inspire others. Often, generic fundraising platforms won't cut it. That's why
Experiment developed the best fundraising site for funding scientific research.
With specific categories like psychology, biology, and neuroscience, Experiment aims to "help fund the next wave of scientific research." The all-or-nothing platform setup requires your campaign to reach its fundraising goal in order for supporters to be charged. This extra motivation challenges supporters to pledge adequate funding, so you can continue making scientific advancements, instead of worrying about securing funding.
How This Fundraising Website Can Help
Experiment’s platform enables researchers to continue focusing on their work instead of spending precious time fundraising to no avail. With more than 47,000 members backing nearly 950 experiments, this fundraising website may be the optimal choice for furthering your cause and funding your mission.
To maximize your use of this fundraising website, follow these simple steps:Start a project and set your fundraising goal.
Get endorsements from colleagues and peers.
Submit your campaign for review by the Experiment team.
Spread the word about your campaign across your personal network.
Once you hit your fundraising goal, you'll receive the funds.
Best of all, it's completely free to
launch a campaign on Experiment's fundraising site. If your campaign is fully funded, you'll be charged an 8% platform fee and a 3-5% payment processing fee.

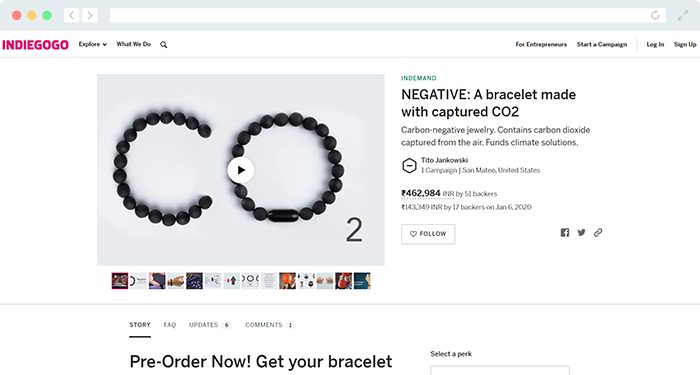
12. Indiegogo | Top Fundraiser Website for Creative Projects
When you've created a unique product and attempt to take it to market, the sooner you rally support and funding, the better. For community projects and innovative tools,
Indiegogo is one of the best crowdfunding websites available for attaining a high-profile reach for creative projects.
Overall, it's a strong option for entrepreneurs and new technology in the earliest stages of development all the way to distribution, from concept to prototype to production to shipment.
How This Fundraising Website Can Help
With more than $1 billion raised on their fundraising website, Indiegogo is a leading platform for entrepreneurship in three primary areas:Tech and Innovation
Creative Works
Community Projects
Indiegogo's crowdfunding campaigns are where groundbreaking products and projects take flight, sometimes long before they hit mainstream availability.
When creating your Indiegogo crowdfunding page, you'll be able to prominently display videos and images that feature your project or product. Then, take it a step further by featuring compelling text that details the purpose behind your project. Plus, Indiegogo offers
a helpful field guide for successful crowdfunding that you can reference at any time to boost your campaign.
Between
these features and more than 9 million backers, your campaign is sure to be a success.

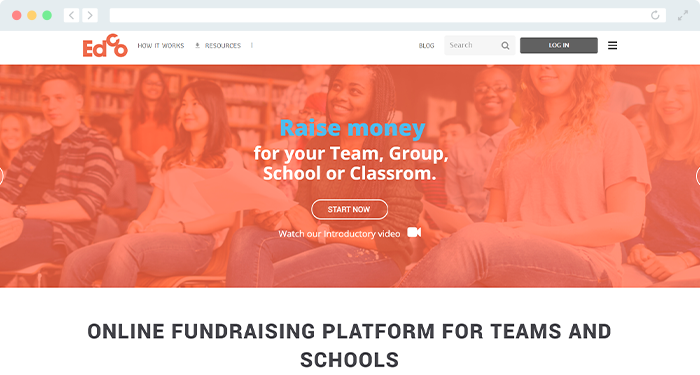
13. EdCo | Best School and Team Fundraiser Website
All too often, one person is responsible for all fundraising responsibilities, especially within the K-12 sector. Instead, make fundraising a team effort and get everyone involved! This is EdCo's mantra with their platform that minimizes the pressure of
hosting crowdfunding campaigns by splitting up the marketing responsibilities.
With
EdCo's team fundraising website, you can set up your
school,
sports team, or club's fundraising page within minutes. Then, get students and parents in on the action with social media sharing features. EdCo works directly with students, teachers, parents, mentors, coaches, and community leaders, so you'll know you're receiving the tailored support you need.
How This Fundraising Website Can Help
EdCo's fundraiser website helps classrooms and teams collect donations from across the entire country. All it takes is persistence and teamwork. Here are a few of
EdCo's features that allow you to take advantage of everything this fundraising website has to offer:Build your team. The more people on your team, the greater your reach will be. Recruit parents and students to participate and ensure everyone does their part in making the campaign a success.
Promote your fundraiser from a central system. Using customizable templates, easily broadcast your campaign on social media and
direct marketing outlets with just a few clicks.
Recycle old campaigns. Once you've created your first campaign page, you'll never have to start from scratch again. This fundraiser website makes it easy to re-engage donors and continue growing your reach.
Best of all, they take care of the payment processing details and provide donation receipts. Any donations that are made on EdCo's fundraiser website are tax-deductible, and you can withdraw raised funds whenever it's most convenient.

14. Kiva | Top Microlending Fundraiser Website
Simply put, microlending is a form of financing that provides small loans to those in need. It's an effective way to raise funds and overcome financial barriers for all types of causes. However, it's most often used to help individuals escape poverty by giving them sufficient financial backing to start small businesses, cover medical expenses, and more.
Through microlending fundraiser websites like
Kiva, people around the world can lend a hand to those in need. Once someone in need is approved for a loan, philanthropic individuals can lend money, which the borrower will repay over time. With all sorts of categories for projects on Kiva's fundraiser website, your mission is sure to find financial backing, regardless of whether it's related to health, agriculture, education, or something else.

How This Fundraising Website Can Help
With nearly 2 million lenders in 77 countries, Kiva allows philanthropic individuals to support the missions that matter most to them. Let's walk through
how this fundraising website connects millions of donors with important projects and causes:Apply through Kiva's fundraising website. Find out if you're prequalified. Then, easily fill out the online application.
Invite supporters. Prove your creditworthiness by inviting your personal and professional networks to lend to you.
Fundraise. Push your Kiva fundraising page live, with your loan visible to nearly 2 million lenders worldwide.
Repay your loan. As funds are collected, repay your loan and any accumulated interest.

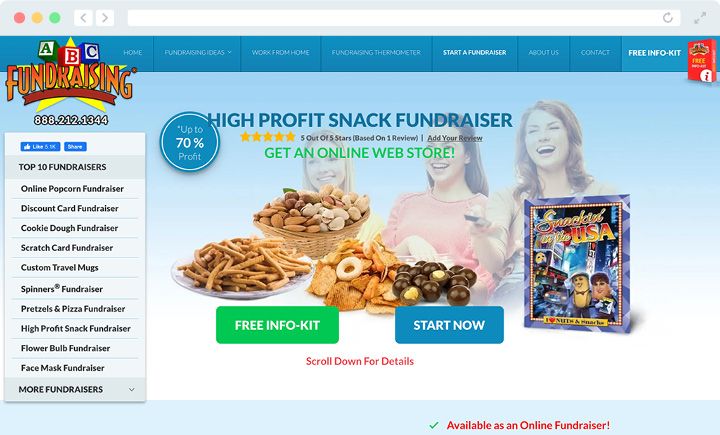
15. ABC Fundraising | Best Product Fundraising Website
Donors love product fundraisers. Why? With a product fundraiser, your donors can buy a product they’re excited about, like
cookie dough, branded travel mugs, or
popcorn, and have their purchase go toward supporting your cause.
The key to setting up a successful product fundraiser is picking the right product fundraising company to work with.
ABC Fundraising offers a wide variety of fundraising products and makes the process of selling, ordering, and delivering those products quick and easy, with an emphasis on helping your organization pull in a profit.
How This Fundraising Website Can Help
ABC Fundraising empowers you to choose products that your supporters will actually want to buy. You can browse through the options on their website and see a projection of what your nonprofit could make with each product.
ABC will also set you up with branded flyers and order forms, and they offer free delivery for many of their products. Plus, you can take your fundraiser online with a fundraising web store designed just for you by ABC.
Selecting the right fundraising website doesn't have to be challenging. Simply use your cause's needs as a guide. There are countless options for you to choose from, so conduct sufficient research and go into the decision with a platform-based mindset. Then, you'll be well on your way to selecting a fundraiser website that helps you exceed your financial goals.
Now that you've thoroughly kickstarted your search for the best fundraiser websites, continue your research by exploring these helpful resources:
Online Fundraising: 10 Ideas with Examples + Bonus Tips. Learn some actionable tips for hosting your next online campaign, so you can make the most of your fundraising platforms.
100+ Unique (And Easy!) Fundraising Ideas. Need ideas that will supercharge your fundraising efforts? Check out this complete list with more than 100 fundraising ideas from Funds2Orgs.
17 Best Online Donation Tools + Software Best Practices. Carry on with your search for the top fundraising platforms with our helpful list of software suggestions, complete with all important details and best practices to follow.
Source - https://blog.donately.com/fundraiser-websites/




































